Totally Pwning the Tapplock Smart Lock (the API way)
tl:dr: Tapplocks api endpoints had no security checks other than a valid token to access any data.This results in anyone with a valid login…
tl:dr: Tapplocks api endpoints had no security checks other than a valid token to access any data.This results in anyone with a valid login (easily obtained by creating an account) being able to manipulate every tapplock available!
The usual suspect…
Yesterday I read the great article by the one and only cybbergibbons about tapplock and totally pwning it and as always I wanted to do it! I cannot do a lot hardware wise (and certainly nothing more than cybergibbons did) so lets check the mobile apps.I downloaded the app and started poking around.First of all no https which is a very bad sign. Then the usual suspects: Direct access object vulnerability. Created a second user and tried accessing the first ones properties: Success!
Can I hack your lock please ?
I did not have any locks (and I am out of IoT budget for this month as my wife has -kindly- informed me), so in order to verify some stuff I reached out to the original reporter who was kind enough to share with me his email (that was all that I wanted and needed as brute forcing ALL accounts would be illegal) and his consent for me to access his details. I also believe this is the first time a twitter DM is used as a GDPR consent

After that I was able to verify that :
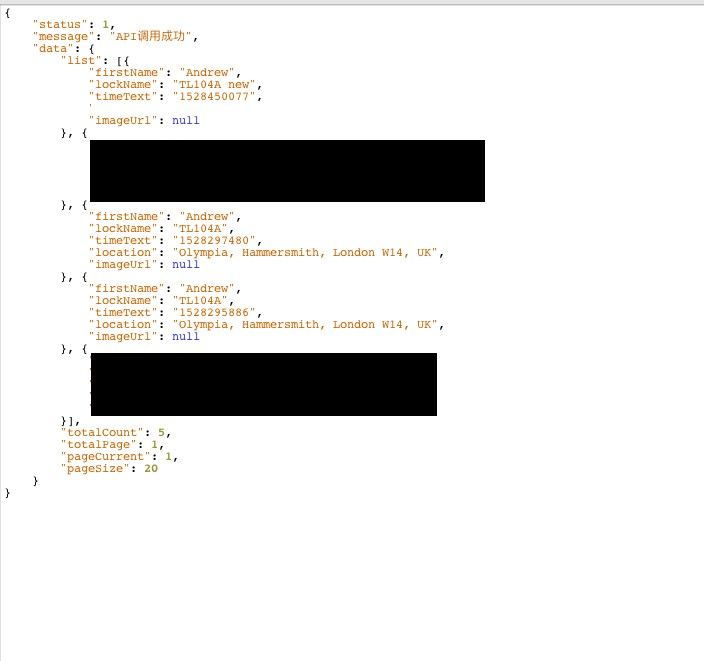
- I could access all info about any lock (with an incremental id that I did not try brute forcing as I had cybergibbons id, and that would be illegal). And by all I mean ALL (key1, key2, serial and everything else). This means that everything was enumerable via simple relationships. (lock -> fingerprint -> user).
- I could share any lock I wanted PERMANENTLY to any account and the lock owner would not be able to remove it (or at least as the original article says have the feeling that he did)
- I could do pretty much everything that you can do with the app by changing some parameters in the http calls as no check other than the one of a valid login is being made.
- There were some hidden API calls that could delete or change a lot of stuff but I did not verify that this data ends up in the lock, as I did not had the time and did not want to bug more cybergibbons.
- I could access really sensitive PII (like the user exact address when he/she unlocked the lock via bluetooth (possibly home address) and email) which is probably a violation of GDPR.
Attack scenario
So after my findings, things look really bad.I could script an attack that would share any lock permanently with my account (or ANY account), then extract all the locks last unlock location, go there and unlock them via the official app! Pentest partners hack was way cooler but in the process we also got a GDPR violation + we also know location now! It feels like we are on a CTF.
Notifications
- 2018/06/14 : Notified tapplock of the findings
- 2018/06/15: Got a reply from tapplock: “We are making a plan to disable the APIs that are related to GDPR sensitive data in the next 24 hours.”
- 2018/06/15: Replied to tapplock for my disclosure procedure.
- 2018/06/16: Tapplock got the API down after pressure because it was exposing GDPR data.
Postmortem:
In here I usually write about how you should buy something from a well known company and how they should respond and some more but not this time. I really have no postmortem on this one. The lock had several flaws and to my understanding they had a great marketing team but a non existent security team. I cannot tell you to buy or not buy anything as I don’t have the authority to do so but I would not buy this lock.